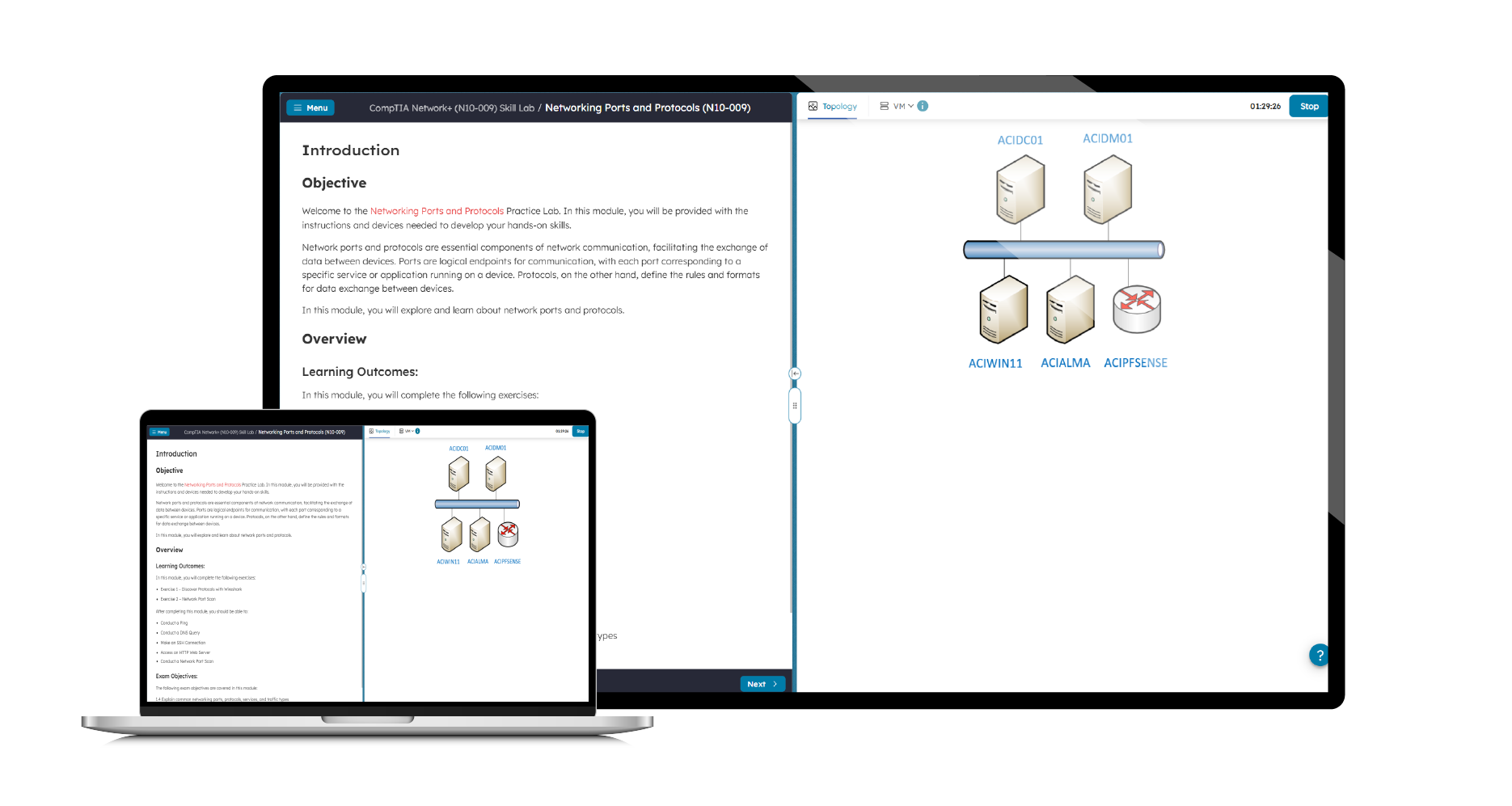
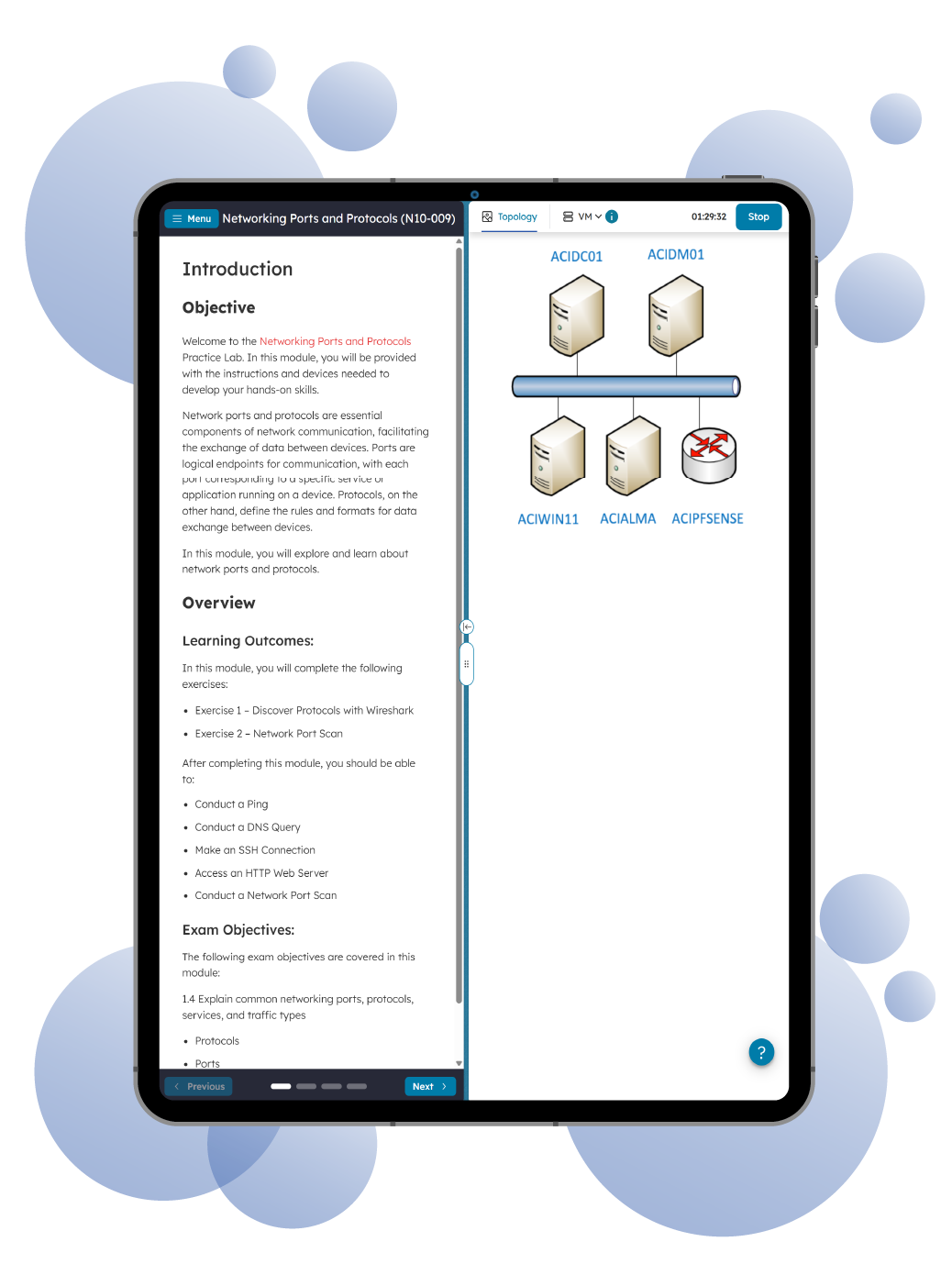
Get hands-on cybersecurity training with the Practice Lab for CompTIA Security+ SY0-701, a real-world lab environment designed to help you master the practical skills required to pass the Security+ SY0-701 certification exam and protect modern IT systems.
This browser-based lab gives you online access to real computer equipment that is networked and fully interactive with no additional software required. Configure devices, run security tools, and complete guided exercises that mirror real-world security scenarios.
Practice Lab for Security+ SY0-701 focuses on the practical application of exam objectives, helping you gain experience in:
- Implementing preventative cybersecurity measures
- Conducting penetration testing and vulnerability assessments
- Securing networks, endpoints, and systems
- Identifying and mitigating threats and attacks
- Applying best practices for risk management and compliance
Each module includes step-by-step instructions to guide you through hands-on tasks, reinforcing key Security+ concepts while building real-world technical skills.